Imagine receiving an email that looks so authentic it could easily be mistaken for a routine work communication. Now, think about how often such emails manage to slip through the cracks of careful scrutiny. This scenario underscores the critical role human error plays in cybersecurity breaches – a reality that became strikingly clear to me during a recent security briefing where a staggering statistic was presented: 85% of breaches involve the 'human element'!
Understanding the Human Element in Cybersecurity
When we talk about cybersecurity, we often think of firewalls, encryption, and sophisticated software. But there's another crucial factor at play: the human element. What does this mean? Simply put, it refers to the role that human behavior plays in cyber breaches. It’s a term that encompasses mistakes, negligence, and even malicious actions by individuals within an organization.
Defining the Human Element in Cyber Breaches
The human element is a significant contributor to cyber incidents. It includes everything from employees falling for phishing scams to inadvertently sharing sensitive information. In fact, a staggering 85% of cybersecurity breaches involve human elements. This statistic, reported by Verizon, underscores the importance of understanding how human actions can compromise security.
Statistics Highlighting the Prevalence of Human Error
Let’s break this down further. Here are some eye-opening statistics:
85% of breaches are due to human error.
With the rise of remote work, phishing attacks have surged. Many employees are now working from home, making them more vulnerable to sophisticated attacks.
Over the past few years, the frequency of user-targeted attacks has increased dramatically.
These numbers reveal a troubling trend. As our work environments evolve, so do the tactics of cybercriminals. They are becoming more adept at exploiting human vulnerabilities.
Examples of Recent High-Profile Breaches
Consider some recent high-profile breaches that were caused by human mistakes:
A major healthcare provider suffered a data breach after an employee clicked on a phishing email, exposing thousands of patient records.
A well-known financial institution faced significant losses when an employee mistakenly sent sensitive information to the wrong recipient.
In another case, a tech giant experienced a breach due to an employee using a weak password, which was easily guessed by hackers.
These incidents illustrate that even the most secure systems can be compromised by human error. It’s a stark reminder that technology alone cannot safeguard against breaches.
The Importance of Recognizing Human Behavior
Why is it essential to recognize the human element in cybersecurity? Because understanding human behavior is key to developing effective security strategies. We need to realize that people are often the weakest link in the security chain. As a cybersecurity expert once said,
"The weakest link in cybersecurity is often the human factor."
Moreover, the art of deception in phishing has become increasingly sophisticated. Cybercriminals are no longer sending generic emails. They craft messages that appear legitimate, often mimicking trusted sources. This makes it harder for employees to spot a scam.
Building a Security-Savvy Workforce
So, what can organizations do? The answer lies in education and training. By investing in ongoing Human Risk Management (HRM), businesses can:
Reduce employee errors that lead to breaches.
Enhance data loss prevention by increasing resilience against targeted attacks.
Demonstrate compliance with key security frameworks.
In conclusion, the human element is a critical factor in cybersecurity. As we navigate an increasingly digital world, we must prioritize training and awareness. After all, protecting our data is not just about technology; it’s about people.
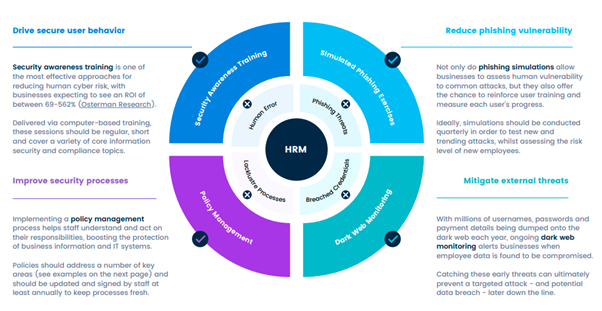
Implementing Human Risk Management (HRM) Strategies
Overview of HRM and Its Objectives
Human Risk Management (HRM) is not just a buzzword; it’s a vital strategy for today’s businesses. At its core, HRM focuses on understanding and mitigating risks that arise from human behavior. Why? Because, according to Verizon, the ‘human element’ is involved in 85% of cybersecurity breaches. That’s a staggering number!
The primary objective of HRM is to create a security-savvy workforce. This means equipping employees with the knowledge and tools they need to recognize and combat cyber threats. It’s about fostering a culture of security awareness that permeates every level of the organization. It’s not just about avoiding breaches; it’s about building resilience.
Key Components of an Effective HRM Program
So, what makes an HRM program effective? Here are some key components:
Education: Regular training sessions are essential. These should be engaging and tailored to the specific needs of your workforce.
Assessment: Periodic evaluations, like phishing simulations, help gauge employee vulnerability and reinforce learning.
Monitoring: Ongoing dark web monitoring can identify exposed credentials, allowing you to act before an attack occurs.
Policy Management: Simplifying processes for tracking employee compliance ensures everyone is on the same page.
Each of these components plays a crucial role in reducing human error, which is often the weakest link in cybersecurity.
Benefits of HRM in Reducing Breaches and Financial Losses
Implementing HRM strategies can lead to significant benefits. Here are a few:
Reduction in Breaches: By educating employees, you can significantly lower the chances of breaches caused by human error.
Financial Savings: Fewer breaches mean less financial loss. Companies can save on fines and recovery costs.
Increased Awareness: As employees become more aware of potential threats, their resilience increases. This is crucial in today’s fast-evolving cyber landscape.
As a security consultant once said,
“Effective Human Risk Management is not just a program; it's a culture change within the organization.”
This statement encapsulates the essence of HRM. It’s about shifting mindsets and behaviors, not just ticking boxes.
Aligning HRM with Compliance Standards
Another important aspect of HRM is its alignment with compliance standards like ISO 27001. This standard emphasizes the importance of risk management in information security. By integrating HRM into your compliance strategy, you not only enhance security but also demonstrate a commitment to best practices.
Incorporating HRM into your compliance efforts can streamline processes and ensure that your organization is not just compliant but also secure. This is a win-win situation!
Introducing Our Managed HRM Service
We’re excited to introduce a new managed HRM service designed to help businesses like yours tackle human cyber risk effectively. This service focuses on:
Preventing user-related breaches and financial losses.
Strengthening data loss prevention through enhanced employee resilience.
Demonstrating compliance with key frameworks.
With our service, you can empower your employees and create a robust defense against cyber threats. It’s time to take action and protect your organization from the inside out!
Creating a Culture of Cyber Awareness
In today's digital world, creating a culture of cyber awareness is more important than ever. With the human element playing a role in 85% of cybersecurity breaches, we must prioritize ongoing training and education. But how do we do that effectively?
The Role of Ongoing Training and Bite-Sized Learning
First, let’s talk about ongoing training. It’s not just a checkbox on a compliance list. It’s a necessity. Regular training sessions keep security practices fresh in the minds of employees. Think about it: if you only learned to ride a bike once, would you still be able to ride it years later? Probably not. The same goes for cybersecurity.
Bite-sized learning is key. Short, engaging modules make it easier for employees to absorb information.
Regular assessments help identify knowledge gaps and reinforce learning.
By implementing these strategies, we can transform our workforce into a security-savvy team. Employees become the first line of defense against cyber threats. They need to know how to recognize phishing attempts and other attacks. Regular training ensures they are prepared.
Implementing Phishing Simulations Effectively
Now, let’s dive into phishing simulations. These are crucial for assessing how vulnerable your employees are to attacks. But how do we implement them effectively?
Start with a baseline: Before launching simulations, understand your current security posture. This helps in measuring improvement.
Create realistic scenarios: Use real-world examples that employees might encounter. This makes the training relatable.
Provide immediate feedback: After a simulation, give employees feedback on their performance. This helps them learn from their mistakes.
Phishing simulations not only test employees but also educate them. They learn what to look for and how to respond. It’s like a fire drill for cybersecurity. You don’t want to wait until there’s a fire to learn how to escape!
Using Dark Web Monitoring to Bolster Employee Security
Another vital component is dark web monitoring. This proactive measure identifies exposed user credentials before they can be exploited. It’s like having a security guard watching over your digital assets.
Identify risks: Regular monitoring helps you spot compromised credentials.
Prevent attacks: By addressing these vulnerabilities, you can prevent potential breaches.
Imagine finding out that your employees' credentials are for sale on the dark web. Wouldn’t you want to act immediately? Dark web monitoring allows us to do just that, giving us a chance to strengthen our defenses before an attack occurs.
“Training shouldn't be a one-time event; it needs to be continuous and evolving.” - Cybersecurity Trainer
Incorporating these elements into your cybersecurity strategy can significantly enhance your organization’s resilience. By focusing on ongoing training, effective phishing simulations, and dark web monitoring, we can create a culture of cyber awareness that empowers employees. They become not just participants but champions of cybersecurity.
Let’s explore interactive training sessions and simulations that strengthen employee cybersecurity awareness. Together, we can build a safer digital environment for everyone.
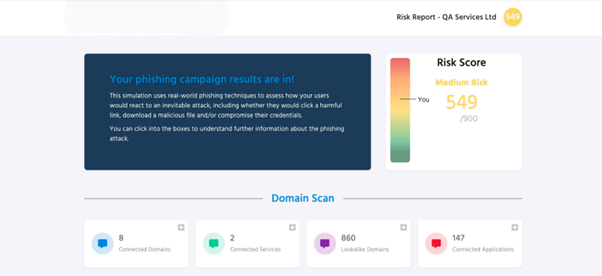
Assessing Your Human Cyber Risk with a Human Risk Report
In today’s digital landscape, the human element is often the weakest link in cybersecurity. Did you know that a staggering 85% of cyber security breaches involve human error? This highlights the urgent need for businesses to understand their vulnerabilities. One effective tool for this is the Human Risk Report (HRR). But what exactly is an HRR, and how can it help your organization?
What is a Human Risk Report (HRR)?
A Human Risk Report is a comprehensive analysis that identifies and assesses the human-related risks within your organization. It provides insights into how employees interact with security protocols and where they might fall short. The HRR helps highlight specific areas of risk, allowing organizations to set benchmarks for improvement.
Think of it this way: if your organization were a ship, the HRR would be the compass guiding you through treacherous waters. It shows you where the leaks are and helps you patch them up before they sink your ship.
Steps to Claim and Benefit from a Free HRR
Claiming your free Human Risk Report is straightforward. Here’s how you can get started:
Visit the website: Go to this link.
Fill out the form: Provide the necessary details about your organization.
Receive your report: Once submitted, our team will analyze your business for vulnerabilities and send you the HRR.
By following these simple steps, you can gain valuable insights into your organization’s human cyber risk. The report will not only identify weaknesses but also provide actionable recommendations to strengthen your security posture.
Understanding Potential Vulnerabilities in Your Organization
Every organization has its unique set of vulnerabilities. These can stem from various sources, including:
Employee behavior: Poor password practices or falling for phishing scams.
Lack of training: Employees may not be aware of the latest threats or best practices.
Outdated policies: Security protocols that haven’t been updated can leave gaps.
Understanding these vulnerabilities is crucial. As the saying goes,
“Knowledge is power; understanding where your risks lie is crucial to building resilience.” - Cybersecurity Analyst
The HRR provides a clear picture of where your organization stands and what steps you can take to improve.
Moreover, the essentials included in the report have a significant impact on your overall security posture. By addressing the highlighted areas, you can prevent user-related breaches, fines, and financial losses caused by human error. This proactive approach not only protects your organization but also builds a culture of security awareness among your staff.
In conclusion, the Human Risk Report is an invaluable tool for any organization looking to bolster its cybersecurity defenses. By understanding and addressing human-related risks, you can create a more resilient workforce. So, why wait? Take the first step towards securing your organization by claiming your free HRR today. It’s time to turn knowledge into action and safeguard your business from potential threats.



