
Aug 28, 2025
What Your Employees Aren’t Expecting: The 5 Cyber Threats They’ll Actually Face in 2025
A few years ago, I (allegedly) locked myself out of my company’s own system by clicking a convincing email—right before a major client presentation. Instead of brushing off that tiny panic attack, I turned it into a mission: what are the cyber threats *employees* are actually up against, the ones an honest mistake could trigger? Turns out, knowing about the big news hacks is one thing; realizing how weird and wily cyber risks for 2025 will be is another. Let’s get off the beaten path and talk about the real threats your people could face next year—and yes, some of them are weirder than you’d imagine. 1. Ransomware Double Extortion: Not Your Old-School Kidnapper Ransomware attacks in 2025 are not the same as the ones your employees might remember from just a few years ago. The game has changed, and so have the stakes. Today’s cybercriminals are using a new weapon: Ransomware Double Extortion. This tactic doesn’t just lock up files and demand payment for their release. Now, attackers also steal sensitive data and threaten to leak it publicly unless their demands are met. It’s a two-pronged attack—one that can cost organizations both money and reputation. How Double Extortion Works Traditional ransomware would encrypt files, making them inaccessible until a ransom was paid. In 2025, the threat has escalated. With double extortion, attackers first steal confidential data before encrypting systems. If the ransom isn’t paid, they threaten to publish or sell the stolen data, causing even more damage. This shift means that even organizations with good backups are at risk—because now, it’s not just about restoring files, but protecting privacy and trust. Who’s in the Crosshairs? According to recent research, Ransomware Attacks 2025 are expected to target critical sectors like healthcare and finance. These industries hold valuable personal and financial information, making them prime targets for double extortion. Attackers know that a data leak in these sectors can cause chaos, disrupt operations, and lead to regulatory fines. The goal is no longer just a quick payday—it’s also about creating maximum leverage and embarrassment. Healthcare: Patient records, insurance details, and even private communications are at risk. Finance: Sensitive financial data, client information, and transaction records are prime targets. Real-World Impact: More Than Just Files Consider the story of a hospital that fell victim to a ransomware double extortion attack. The attackers didn’t just lock up medical files—they also stole personal photos from the CEO’s email. When the hospital refused to pay, the hackers leaked the CEO’s vacation pictures online. The organization had prepared for file loss, but not for the embarrassment and privacy invasion that followed. This anecdote highlights how Ransomware Double Extortion can impact both business operations and personal lives. Why Ransomware Tops the Threat List It’s no surprise that experts predict over 45% of organizations will rank ransomware as their number one cybersecurity threat in 2025. The cost of cybercrime is rising, and double extortion campaigns are a major driver. As Kevin Mitnick famously said: 'Ransomware has morphed far beyond its original playbook—now leaks are the real poison.' — Kevin Mitnick With the growing sophistication of these attacks, organizations in all sectors—especially healthcare and finance—must prepare for more than just locked files. The threat now includes public exposure, regulatory penalties, and lasting damage to trust. Cybersecurity Threats 2025 are evolving, and ransomware double extortion is leading the charge.2. AI-Driven Cyberattacks: When Bots Go Bad Artificial intelligence was once hailed as the ultimate shield in the fight against cybercrime. But as we move into 2025, AI is no longer just a defender—it’s become a weapon for attackers, too. The rapid integration of AI in Cybersecurity has created a new battlefield, where bots are outsmarting employees and security teams alike. AI Cybersecurity Threats: Smarter Phishing, Deepfakes, and Automated Attacks Hackers are now using AI to craft highly convincing phishing emails, generate realistic deepfake videos, and automate attacks at a scale never seen before. These AI-driven cyberattacks can adapt in real-time, learning from failed attempts and quickly changing tactics. Employees are no longer just dodging suspicious links—they’re being targeted by code that learns and evolves. AI-powered phishing: Attackers use AI to analyze company language, mimic writing styles, and create emails that look exactly like they’re from trusted colleagues or executives. Deepfake deception: Video and voice deepfakes are now so realistic that employees may struggle to tell the difference between a real request and a fake one. Imagine an AI-generated voice clone of your CEO calling the help desk—would your team spot the fraud before handing over sensitive information? Automated malware: AI can automate the creation and deployment of malware, allowing attacks to scale rapidly and bypass traditional security measures. AI in Cybersecurity: Playing for Both Teams The original promise of Cybersecurity AI Integration was to help organizations detect threats faster and respond automatically. Today, AI is being used on both sides of the fight. As Nicole Perlroth puts it: 'Security teams in 2025 must outsmart adversarial AI—not just human hackers.' This means security professionals now face not only human adversaries but also intelligent, adaptive bots. AI-driven attacks can probe for weaknesses, evade detection, and even mimic legitimate user behavior to slip past defenses. Double-Edged Sword: AI Detection and Response Tools AI-powered detection and response tools are essential for modern cybersecurity, but they’re not foolproof. Attackers are developing adversarial AI designed to trick these systems, making it a constant game of cat and mouse. The same technology that helps spot threats can also be manipulated to overlook them. Pro: AI can analyze massive amounts of data, flagging suspicious activity in real-time and automating incident response. Con: Adversarial AI can exploit blind spots in detection algorithms, making attacks harder to spot and stop. As AI becomes more deeply woven into both attack and defense strategies, employees must be prepared for threats that are faster, smarter, and more convincing than ever before. The rise of AI Cybersecurity Threats means that traditional awareness training may not be enough—organizations need to rethink how they prepare their teams for a world where bots can be both friend and foe. 3. The Human Element: Oops Moments and How to Dodge Them When it comes to cybersecurity, the biggest risk isn’t always a shadowy hacker or a sophisticated virus—it’s often a simple mistake made by a real person. Human error cybersecurity incidents are the silent partner in almost every major breach. In fact, a staggering 88% of breaches involve a human slip-up, and 68% are directly caused by employee actions. As cybersecurity expert Rachel Tobac puts it: "Humans: still the most hackable operating system in cyberspace." Phishing and Social Engineering: Outsmarting the Human Firewall Attackers have learned that it’s easier to trick a person than to break through a well-defended network. Phishing and social engineering are the top tactics, with criminals crafting emails, texts, and even phone calls that look and sound legitimate. These messages often use real-world events or urgent requests to convince employees to click a link, download an attachment, or share sensitive information. The IT department’s unofficial motto could be, “Seriously, don’t click that weird link.” Phishing: Fake emails or messages that look real, asking for login details or prompting a dangerous download. Social Engineering: Attackers impersonate trusted people—like a boss or IT support—to manipulate employees into giving up information. With remote work cyber risks on the rise, these attacks are becoming even more effective. Employees working from home may be distracted, isolated, or using personal devices, making them prime targets for phishing and credential theft. Remote Work: New Opportunities for Old Mistakes Remote work setups have expanded the attack surface for cybercriminals. Employees often use unsecured Wi-Fi, mix personal and work devices, or store sensitive files in the wrong place. These basic mistakes can lead to accidental data loss or exposure. In 2025, attackers are expected to double down on targeting remote workers, knowing that home networks and personal habits are often less secure than office environments. Unsecured Wi-Fi: Home networks may lack strong passwords or encryption. Device Sharing: Family members may use the same device, increasing risk. Cloud Storage Confusion: Files saved in the wrong folder or shared with the wrong person can lead to leaks. Employee Cybersecurity Awareness: The Best Defense While expensive hardware and software are important, employee cybersecurity awareness and training are often the most effective defenses. Regular, realistic training helps staff recognize phishing attempts, avoid credential theft, and understand the risks of remote work. Since it takes an average of 194 days to identify a breach, early detection by alert employees can make all the difference. Simulated phishing campaigns to test and educate staff Clear reporting channels for suspicious emails or activity Frequent reminders: “If in doubt, don’t click!” Human error will always be part of the cybersecurity equation, but with the right awareness and habits, employees can transform from the weakest link into the strongest defense.4. Supply Chain Shenanigans: When Your Vendors Are the Backdoor When most employees think about cybersecurity risks for organizations, they picture hackers targeting their own company’s network. But in 2025, the real danger may be lurking in the supply chain. As businesses rely more on third-party vendors for everything from software to coffee supplies, supply chain cybersecurity risks are rising fast—often in ways employees never expect. Supply chain disruptions aren’t just about late shipments or hardware delays anymore. Today, every third-party partner is a potential cyber backdoor. A single compromised vendor can open up access to your entire business network. As cybersecurity journalist Brian Krebs puts it: “The more we outsource, the more invisible doors we unlock.” Third-Party Partners: The Weakest Link Many organizations invest heavily in securing their own systems, but overlook the cybersecurity vulnerabilities 2025 introduced by external partners. Products and services your company never built can become the weakest link. Ask anyone who’s had to scramble after a vendor data leak—these incidents can be just as damaging as direct attacks. Example: The SolarWinds and Kaseya breaches showed how attackers can compromise thousands of organizations by targeting a single supplier. Reality check: Even a small vendor, like your morning coffee supplier, could be the entry point for hackers. If their database is hacked, it could lead to your payroll system being exposed. Stranger things have happened! Why Supply Chain Cybersecurity Risks Are Growing In 2025, organizations are more interconnected than ever. Cloud services, SaaS platforms, and outsourced IT support are now business essentials. This increased dependency means that a security flaw in any partner’s system can quickly become your problem. According to recent research, supply chain disruptions and vulnerabilities are among the most significant emerging risks for organizations today. Vendor Risks: The Overlooked Source of Cyber Incidents Vendor risks are often overlooked, but they’re a leading source of cyber incidents. Attackers know that third-party suppliers may not have the same security standards as your own company. Once inside a vendor’s network, they can “hop” into yours—sometimes without detection for months. These cybersecurity vulnerabilities 2025 are notoriously hard to spot until it’s too late. Attacks can propagate from compromised vendors to your core business systems. Supply chain vulnerabilities are often hidden and difficult to identify in advance. Continuous monitoring of vendors is now a security must-have, not a maybe. What Organizations Should Do To defend against supply chain cybersecurity risks, organizations must: Vet all third-party vendors for security practices before onboarding. Continuously monitor vendor activity and access to sensitive data. Establish clear protocols for responding to vendor-related incidents. In 2025, every business relationship is a potential cyber risk. Monitoring and managing these connections is essential for staying secure in an increasingly interconnected world.5. Cybersecurity Awareness Training: The Only Antivirus for Human Error In 2025, the most advanced security software and hardware are only as effective as the people using them. As cybercrime costs are projected to reach a staggering $10.5 trillion globally, businesses can no longer rely solely on technology to protect their data and operations. Instead, Cybersecurity Awareness Training has become the frontline defense against the most common—and costly—threat: human error. While firewalls and antivirus software are essential, they cannot stop an employee from clicking a malicious link or falling for a cleverly disguised phishing email. As Theresa Payton, former White House CIO, puts it: "Awareness programs are as important as antivirus. Pretend you’re allergic to clicking links." This mindset is at the heart of modern Cybersecurity Awareness Programs. Unlike the outdated annual slideshow, today’s training is continuous, interactive, and even enjoyable. Companies are embracing phishing simulation games, real-time threat challenges, and microlearning modules that fit seamlessly into the workday. These proactive approaches not only teach employees to spot suspicious emails and handle data safely, but also prepare them to act quickly and effectively if a breach occurs. The benefits of investing in Employee Cybersecurity Awareness are clear. According to recent research, the average time to identify a data breach is 194 days, and the full lifecycle from detection to containment can stretch to 292 days. However, organizations with robust, ongoing training programs consistently detect and contain incidents much faster. This speed can mean the difference between a minor disruption and a major financial or reputational loss. Engaging training also helps reduce the overall number of incidents. Employees who regularly participate in clever simulations and microlearning become more alert and skeptical—like a spam filter with a double shot of espresso. They are less likely to fall for scams, more likely to report suspicious activity, and better equipped to respond if something does go wrong. In short, Cybersecurity Best Practices become second nature. As cyber threats evolve, so must the way companies educate their teams. The most successful organizations in 2025 will be those that treat cybersecurity awareness as an ongoing journey, not a one-time event. By making training continuous, relevant, and even fun, businesses empower their employees to be the strongest link in the security chain. In a world where human error remains the biggest vulnerability, effective Cybersecurity Awareness Training is truly the only antivirus that matters. In conclusion, while no system is foolproof, a well-trained workforce dramatically reduces risk and limits the impact of inevitable incidents. As cybercrime continues to rise, investing in proactive, engaging employee training is not just a best practice—it’s a business imperative for 2025 and beyond. TL;DR: Employees remain the first and last line of defense—cyber threats in 2025 will evolve, but with real awareness, even the quirkiest risks can be managed. (Pro tip: Trust but always verify that email from 'the boss.' You never know when it’s a trap.)
13 Minutes Read

Aug 28, 2025
More Than Oops: The Hidden Ways Employee Mistakes Threaten Your Business (and What to Do About It)
Some mornings, it only takes one typo to send your company scrambling—for me, it was an extra zero in payroll that nearly tanked the budget (don’t ask). But here’s the gut-punch: small, all-too-human mistakes like mine happen every day, costing businesses far more than embarrassment. From wild burnout rates to head-scratching HR fines, this post explores the messier, hidden fallout of employee errors, and what you can actually do—besides crossing your fingers. Wild Card: Imagine if your business ran on autopilot—no slipups, no oversights. But would anyone even show up? Are mistakes just the price of being human at work? The Snowball Effect: Tiny Errors, Titanic Consequences (Human Error Impact) It’s easy to dismiss a small mistake at work—a missed checkbox, a misplaced decimal, or a forgotten attachment. Yet, these seemingly minor slip-ups can trigger a chain reaction, leading to consequences far beyond a simple correction or apology. According to human error statistics 2025, a staggering 80% of business process failures are caused by human mistakes. This figure highlights just how vulnerable organizations are to everyday errors. Consider the cost of employee mistakes in real-world terms. One infamous example is the accounting typo that led to a $225 million loss for a major firm. A single extra zero—or the lack of one—can transform a routine transaction into a financial disaster. Such financial losses from employee errors don’t just impact the bottom line; they can also damage a company’s reputation and erode client trust. Why Small Errors Spiral Out of Control Why do common workplace errors escalate so quickly? The answer lies in the interconnected nature of modern business systems. When one person makes a mistake, it often goes unnoticed until it interacts with other processes—like a domino effect. Deadlines, high workloads, and stress only increase the risk. For example: Unchecked data entry can corrupt entire databases, affecting reports and decisions. Missed safety steps can lead to accidents or compliance violations. Misfiled documents can delay projects and frustrate clients. The employee mistakes business risk is often underestimated until it’s too late. What starts as a minor oversight can snowball into lost contracts, regulatory fines, or even legal action. The true cost of employee mistakes includes not just immediate losses, but also the time and resources spent on damage control. The Myth of Perfection It’s tempting to believe that perfection is the answer—if only every employee could avoid mistakes, the business would be safe. However, obsessing over every slip-up can create a culture of fear and hesitation, making things worse. As usability expert Donald Norman wisely said: "We can’t eliminate mistakes, but we can design workplaces that make the right action easier than the wrong one." Understanding the employee mistakes business risk means recognizing that errors are inevitable. The key is to build systems and cultures that catch mistakes early, minimize their impact, and turn lessons into improvements. In today’s fast-paced environment, even the smallest error can have titanic consequences—so awareness and prevention are more important than ever. Burnout: The Quiet Catalyst for Costly Workplace Mistakes Employee burnout levels are quietly fueling a surge in workplace errors that can threaten any business. Burnout is more than just feeling tired—it’s a state where employees operate on “autopilot,” making mistakes they would never normally make. Recent research shows that 64% of employees report feeling burned out at least weekly. This chronic exhaustion doesn’t just sap morale; it directly increases the risk of costly errors that can slip under the radar until it’s too late. When burnout sets in, the impact is immediate and far-reaching. Absenteeism jumps by 23%, and healthcare spending soars as employees struggle with stress-related illnesses. These numbers aren’t just statistics—they represent real risks to business stability and productivity. The workplace errors impact business in ways that go beyond simple “oops” moments. Missed deadlines, forgotten tasks, and compliance slip-ups can all be traced back to overworked, disengaged teams. Employee Disengagement: The Hidden Multiplier of Mistakes Burnout and employee disengagement go hand in hand. Today, only 30% of employees feel truly engaged at work, a record low that compounds the cost of employee mistakes. Disengaged employees are more likely to overlook details, ignore safety protocols, or miss critical communications. As Marcus Buckingham notes: "A disengaged team doesn’t just slow down—mistakes multiply." When engagement drops, so does attention to detail. The employee disengagement impact is felt in every department, from customer service to compliance, amplifying the risk of expensive errors. Personal Anecdote: When Burnout Hits Home Consider a real-world example: After months of chronic overtime, the author’s team missed a crucial contract renewal. The culprit? Mental fog from burnout. No one caught the reminder email, and the oversight led to lost revenue and a scramble to repair the client relationship. This is a classic case of how employee engagement challenges and burnout can quietly sabotage even the most diligent teams. Mistakes Are Contagious in a Burned-Out Team Burnout doesn’t just affect individuals—it spreads through teams like a bad cold. When one employee starts making errors, others often follow, either through distraction or by picking up extra work to cover for absent colleagues. This creates a cycle where workplace errors impact business productivity and well-being, driving up business risk assessment numbers and increasing costs across the board. 64% of employees report weekly burnout 23% increase in absenteeism due to burnout Only 30% of employees are actively engaged Understanding and addressing burnout is essential to reducing costly mistakes and protecting your business from hidden risks.Compliance Catastrophes: The Lurking Financial Tsunami from HR Slipups For many small businesses, HR compliance challenges are like hidden reefs—easy to overlook until disaster strikes. The numbers are sobering: small businesses lose an average of $10,000 per year from HR non-compliance alone. But that’s just the tip of the iceberg. When HR compliance penalties go unchecked, costs can quickly escalate into the millions, threatening the very survival of a business. How Innocent Mistakes Become Expensive Nightmares It’s easy to think of compliance as a box to check, but the reality is far more complex. Even a single overlooked regulation or outdated policy can trigger a cascade of issues. Consider a hypothetical: What if your employee handbook hasn’t been updated since 2015? That seemingly minor oversight could be a compliance time bomb, exposing your business to lawsuits, audits, and regulatory fines. "HR is either your first line of defense—or your weakest link." – Patty McCord Manual Data Entry: The Hidden Risk Multiplier Manual processes are a major source of employee mistakes business risk. Research shows that manual data entry is up to 100 times more error-prone than automated systems. Each typo or missed field can lead to incorrect payroll, misreported taxes, or even data breaches. The costs of a data breach—both in fines and lost trust—can be devastating, especially for small businesses with limited resources. Why Small Business HR Challenges Carry Outsized Impact Regulatory Complexity: With ever-changing labor laws, staying compliant is a moving target. Resource Constraints: Small teams often juggle multiple roles, increasing the risk of oversight. Compliance Risk Management: Proactive management isn’t just about avoiding fines—it’s about protecting sensitive employee data and company reputation. Potential Penalties: The Real Cost of Non-Compliance Annual average loss: $10,000 for small businesses Major penalties: Can reach millions for severe violations Data breach costs: Fines, legal fees, and reputation damage Ignoring compliance risk management can turn a small HR error into a full-blown financial tsunami. Employee mistakes in compliance—whether due to outdated policies or manual data entry—can spiral into larger business risks, threatening both financial stability and long-term growth.The Slipstream of Disengagement: From Quiet Cracking to Productivity Crashes In the evolving landscape of workplace culture 2025, a subtle yet powerful trend is reshaping how companies experience risk: the phenomenon of quiet cracking. Unlike the more visible forms of employee disengagement, quiet cracking describes a silent retreat—where over half of U.S. workers are pulling back from their roles, often triggered by job insecurity or a lack of growth opportunities. This disengagement is not just a morale issue; it is a direct threat to business performance and resilience. Quiet Cracking: The Hidden Cost of Disengagement Recent research highlights that over 50% of the workforce now shows signs of quiet cracking. The employee disengagement impact is staggering: companies lose an estimated 34% of each disengaged employee’s annual salary in lost output, errors, and missed opportunities. As Josh Bersin aptly puts it: “Engagement isn’t a party trick—it’s an insurance policy against mistakes.” Disengaged employees are more likely to make costly mistakes, overlook details, and contribute to a culture where errors become normalized. Real-World Ripple Effects Consider the experience of a peer’s business that shifted to remote work without any re-onboarding or adaptation. Within weeks, avoidable errors surged—deadlines were missed, client information was mishandled, and team morale plummeted. This scenario is a textbook example of how employee engagement challenges can quickly escalate into operational risks and financial losses. Engagement Mistakes to Avoid Many organizations fall into common traps that worsen the employee mistakes cost: Ignoring hybrid work needs: Failing to support remote and hybrid employees leads to isolation and confusion. Forgetting professional development: Employees who see no path for growth are more likely to disengage and underperform. One-size-fits-all policies: Uniform approaches ignore individual needs and circumstances, fueling quiet cracking. Adapting to the New Engagement Reality The employee disengagement impact extends far beyond lost productivity. It increases error rates, damages reputation, and raises compliance risks. As employee engagement challenges shift rapidly in the 2025 workplace, leaders must recognize that preventing mistakes requires more than rules—it demands adaptive, inclusive engagement strategies that address the root causes of quiet cracking. Don’t Just Fix—Rethink: Preventing Employee Mistakes Without Killing Innovation When it comes to employee mistakes prevention, the goal is not to create a workplace where errors are impossible. Instead, the focus should be on building a culture where employees feel supported to learn, grow, and innovate—without putting the business at unnecessary risk. Too often, organizations respond to mistakes with stricter rules and closer monitoring, but this can stifle creativity and lead to a fearful, less productive environment. As Amy Edmondson wisely said, "The businesses that bounce back fastest are the ones that encourage learning, not blame." Research shows that employee training reduces risks and supports business safety. In fact, companies that invest in proper training programs cut the average cost of data breaches by $260,000. This is a clear sign that employee training effectiveness is not just about compliance—it’s about empowering employees to make smarter decisions and feel confident in their roles. When employees understand the “why” behind policies and procedures, they are less likely to make anxiety-driven mistakes and more likely to contribute positively to the company’s goals. But employee mistakes risk mitigation is not about policing every move. Instead, it’s about creating safety nets that catch small errors before they become big problems. Smart technology, such as automated alerts and access controls, can help prevent costly slip-ups without micromanaging staff. Open feedback channels encourage employees to report near-misses and mistakes, turning potential disasters into valuable learning moments. Rewarding transparency and treating errors as opportunities for growth helps build a resilient organization. It’s important to remember that perfection is unrealistic. Employee behavior risk assessment must account for human nature. If your workplace demanded zero mistakes, would your best idea have ever happened? Innovation thrives in environments where people feel safe to experiment, even if that means occasionally getting it wrong. The most successful businesses strike a balance between employee mistakes solutions and creative freedom, using training and compliance management as tools for both safety and growth. In conclusion, preventing employee mistakes is less about rigid control and more about thoughtful support. By investing in effective training, leveraging smart technology, and fostering a culture of open communication, organizations can reduce the business impact of employee mistakes while still encouraging innovation. After all, the path to progress is paved with both successes and well-managed missteps. TL;DR: Employee mistakes are inevitable, but understanding root causes (culture, stress, poor training) can turn risk into opportunity. With better engagement, clear policies, and smarter prevention, you don’t just put out fires—you help your business thrive.
11 Minutes Read
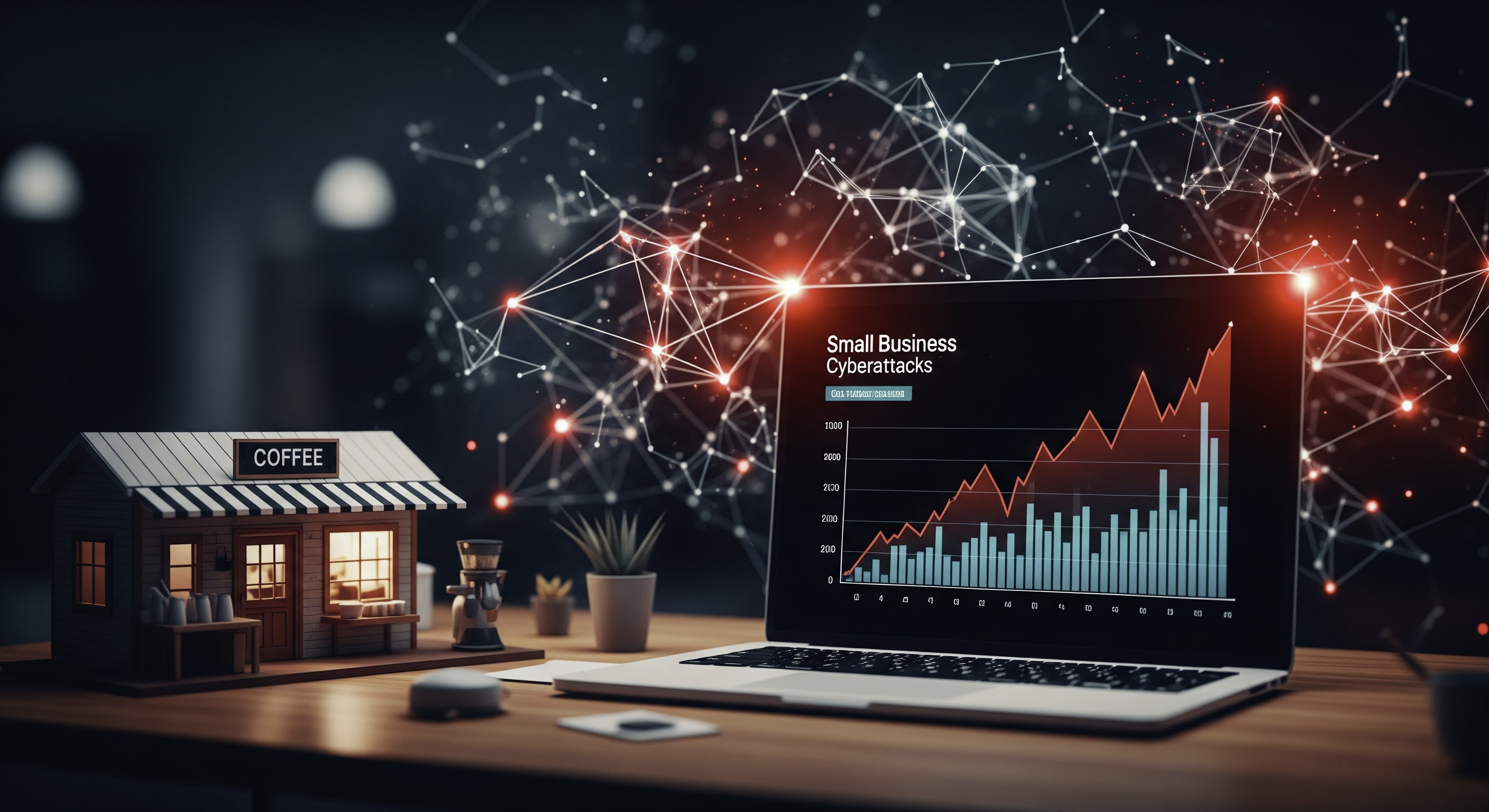
Jun 6, 2025
Behind the Firewall: Startling Small Business Cybersecurity Statistics for 2025 (And Why They Matter More Than Ever)
Last Thursday, while locking up my family’s café after closing, my phone buzzed: an old college friend had just lost every customer record to a ransomware attack. His bakery, just across town, went from thriving to paralyzed overnight. Most people think cybercriminals go after big fish—but in 2025, the sharks are in the shallow end. The numbers don’t lie, but what they mean (and why they matter) is a whole other story—one small businesses can’t afford to ignore. 1. Cybersecurity Threats: The Foe No One Saw Coming Cybersecurity threats have quietly become one of the most pressing issues for small businesses today. While headlines often focus on attacks against massive corporations, the reality is that small and medium-sized businesses (SMBs) are now prime targets. The days when only the Fortune 500 had to worry about hackers are long gone. In 2025, the landscape of Small Business Cybersecurity is more unpredictable—and dangerous—than ever. Ransomware attacks and phishing scams have become the new normal on Main Street. Research shows that 82% of ransomware attacks in 2021 were against companies with fewer than 1,000 employees. That’s not just a blip—it’s a clear sign that cybercriminals are shifting their focus. Small businesses, often seen as having weaker defenses, are now the low-hanging fruit. In fact, 46% of all cyber breaches impact businesses with fewer than 1,000 employees. These aren’t just statistics; they represent real companies, real losses, and real disruption. It’s easy to underestimate the risk. Many SMB owners believe that their size makes them invisible to hackers. However, the numbers tell a different story. 43% of all cyberattacks target small businesses. This isn’t about paranoia—it’s about facing facts. The digital world has changed, and so have the rules of engagement. Why are small businesses so attractive to cybercriminals? The answer is simple: perceived vulnerability. Many SMBs lack dedicated IT teams or formal cybersecurity policies. Social engineering tactics, like phishing emails, are especially effective when staff aren’t trained to spot them. Ransomware attacks—where hackers lock up a company’s data and demand payment—can cripple operations overnight. For a small business, even a short disruption can be devastating. A quote from Theresa Payton, former White House CIO, captures this shift: ‘Cybercriminals aren’t just targeting the big leagues—they’re coming for small businesses because they’re usually the easiest to crack.’ The impact of these Cybersecurity Threats goes beyond lost data. There’s the cost of downtime, the expense of recovery, and the damage to reputation. Studies indicate that the average cost of a small business data breach in 2025 is climbing, making prevention more important than ever. Sometimes, the threat feels so real that it changes how businesses operate. Take, for example, a local bookstore owner who still uses pen and paper for transactions. At first glance, it might seem like nostalgia. But dig a little deeper, and there’s a story: after a colleague’s business was hit by ransomware, the owner decided that staying offline was the safest bet. It’s a small act of resistance in a world where digital convenience comes with hidden risks. As Cybersecurity Statistics for 2025 continue to reveal, the threat landscape is evolving. Ransomware attacks and social engineering are no longer rare events—they’re the new reality for small businesses everywhere. The numbers are clear, but the real challenge is making sure every business owner takes them seriously. 2. Data Breach Dominoes: When One Falls, Who’s Next? When it comes to Data Breach Statistics for small businesses, the numbers in 2025 are more than just alarming—they’re a wake-up call. The landscape has shifted, and the cost of breaches is no longer something only big corporations worry about. In fact, the average small business data breach now costs $120,000. For many family-owned shops or local service providers, that’s not just a setback; it’s a potential end to years of hard work. Research shows that 60% of small businesses that suffer a cyberattack shut down within six months. It’s a statistic that’s hard to ignore. The aftermath of a breach goes beyond the immediate financial hit. There’s the loss of customer trust, a damaged reputation, and the very real possibility of never reopening. When a local business closes, it’s not just the owners and employees who feel the impact. The entire neighborhood can lose a gathering spot, a trusted service, or a piece of its identity. Ransomware attacks are a particular threat. Studies indicate that ransomware costs small businesses an average of $35,000 per incident. For many, that’s more than a year’s profit wiped out in a single moment. And it’s not just about the ransom itself. There are costs tied to downtime, lost data, and the scramble to recover operations. Sometimes, the savings meant for growth or emergencies are gone overnight. To put it in perspective, imagine your favorite neighborhood coffee shop. Maybe it’s the place where you grab your morning latte, catch up with friends, or get some work done. Now, picture what would happen if that shop suffered a data breach. Suddenly, your loyalty points are gone. Worse, your payment information might be exposed. The shop’s owners are left dealing with angry customers, potential legal issues, and a financial hole that’s hard to climb out of. Would you feel safe going back? Would the shop even survive the fallout? It’s not just a hypothetical. According to recent data, 43% of all cyberattacks target small businesses, and 46% of breaches impact companies with fewer than 1,000 employees. The domino effect is real. One breach can disrupt a local economy, causing a ripple that spreads far beyond the initial victim. As cybersecurity journalist Brian Krebs puts it: “The fallout from a single data breach can ripple across communities, not just companies.” The numbers are clear. The cost of breaches is rising, and the risks are no longer abstract. For small businesses, a single successful attack can mean the difference between thriving and closing for good. The community impact is just as significant as the financial one, making cybersecurity a priority that can’t be ignored. 3. Cybersecurity Awareness: The Invisible Shield Too Many Forget Cybersecurity Awareness is often described as the invisible shield for small businesses, yet it remains one of the most overlooked aspects of Small Business Cybersecurity. Despite the growing number of cyber threats, research shows that 80% of small businesses still do not have a formal cybersecurity policy in place as of 2025. This statistic alone highlights a major gap in preparedness, leaving many organizations exposed to significant Cybersecurity Risks. It’s easy to assume that technology alone can protect a business, but the reality is more nuanced. Human error is frequently the weakest link. In fact, 30% of small business data breaches are tied directly to stolen credentials. This isn’t just a number—it’s a reflection of everyday habits and oversights. Consider the all-too-common scenario: a CEO, pressed for time, jots down her password on a sticky note and leaves it on her desk. It sounds almost cliché, but it’s a true story (names changed to protect the innocent). This simple act can open the door to attackers, no matter how robust the firewall or antivirus software may be. “Security isn’t just a technical challenge—it’s a human one.” – Bruce Schneier, security expert This quote rings especially true for small businesses, where employees often wear multiple hats and cybersecurity training can feel like an afterthought. Many workers experience what could be called “training fatigue.” Why do people skip security seminars? Maybe it’s because they’re always scheduled during lunch, or perhaps the content feels repetitive and disconnected from daily tasks. Whatever the reason, the result is the same: gaps in Cybersecurity Awareness that attackers are all too ready to exploit. The numbers are hard to ignore. With 80% of small businesses lacking a formal cybersecurity policy, and 30% of breaches linked to weak or stolen passwords, it’s clear that policy and education are as critical as any technical Cybersecurity Solutions. Yet, the human element—those everyday choices and habits—remains the most unpredictable factor. Passwords scribbled on sticky notes, reused across multiple accounts, or shared informally among team members, all contribute to a landscape where Cybersecurity Risks are amplified. Anecdotes like the sticky note incident make these risks tangible. They serve as reminders that Cybersecurity Awareness isn’t just about compliance or ticking boxes—it’s about real people making real decisions, sometimes in a hurry, sometimes without understanding the consequences. And while technology continues to advance, the need for ongoing education and practical, relatable training remains as important as ever. In the end, small businesses must recognize that Cybersecurity Awareness is not a one-time project, but an ongoing process. Policies, training, and a culture of vigilance are the invisible shields that can make all the difference in today’s digital landscape. 4. Cybersecurity Trends in 2025: Old Threats, New Tricks Cybersecurity Trends in 2025 are shaping up to be a mix of the familiar and the unexpected. While some Cybersecurity Threats have been around for years, their methods are evolving, and the risks for small businesses are growing. The numbers are hard to ignore: research shows that 93% of company networks can be penetrated by hackers. That’s almost everyone. For small and midsize businesses (SMBs), the situation is even more concerning—75% of SMBs experienced at least one cyber attack in the past year. These Cybersecurity Risks are not just statistics; they’re a daily reality for organizations of all sizes. One of the most persistent Cybersecurity Threats is social engineering. In 2025, it’s not just phishing emails or suspicious links. Attackers are using multi-stage attacks—layering tactics like phone calls, fake websites, and even impersonation to trick employees and bypass security controls. It’s a reminder that old tricks are getting new upgrades. The classic malware attacks haven’t disappeared either. Instead, they’re becoming more sophisticated, often hiding in plain sight or using legitimate tools to spread within networks. For SMBs, the challenge is especially daunting. Studies indicate that 43% of all cyberattacks target small businesses, and the consequences can be severe. The average cost of a small business data breach in 2025 is estimated at $120,000, while ransomware incidents alone cost an average of $35,000 per attack. Yet, despite these risks, 80% of small businesses still do not have a formal cybersecurity policy. It’s a gap that attackers are eager to exploit. What’s driving the surge in successful attacks? Part of the answer lies in the complexity of modern business networks. With more devices connected than ever—including everything from laptops to obscure IoT coffee machines—there are simply more doors for attackers to try. The question isn’t just “Will they get in?” but “Where will they strike next?” The idea of hackers targeting a smart coffee machine might sound far-fetched, but in 2025, it’s not entirely out of the question. Sometimes, the most unexpected entry points become the weakest links. As Katie Moussouris, a noted cybersecurity expert, puts it: 'Cyber defenses are only as strong as their weakest point—which is too often overlooked.' This reality is reflected in the numbers. Even as awareness of Cybersecurity Risks grows, the ability for hackers to penetrate nearly all networks illustrates the ongoing challenge. Attackers are adapting, and so must defenders. Multi-stage attacks, persistent malware, and the creative use of everyday technology all signal a need for constant vigilance. Looking ahead, the unpredictability of Cybersecurity Trends keeps everyone guessing. Will attackers pivot to even more obscure devices? Will new forms of social engineering emerge? The only certainty is that the landscape will keep changing, and businesses—especially SMBs—will need to stay alert to both old threats and new tricks. 5. Building Smart Defenses: From Overwhelm to Action For many small businesses, the world of cybersecurity can feel overwhelming. The statistics paint a stark picture: nearly half of all cyberattacks target small businesses, and the average cost of a breach is now $120,000. But while the risks are real, the path to better protection doesn’t have to be complicated or expensive. In fact, building smart defenses is less about grand gestures and more about consistent, practical steps. Cybersecurity Awareness is the first step, but it’s not enough on its own. Knowing the risks is important, yet action is what actually prevents disaster. Research shows that 80% of small businesses still lack a formal cybersecurity policy, and 30% of breaches happen because of stolen credentials. These numbers highlight a simple truth: most threats exploit basic oversights, not sophisticated weaknesses. So, what does action look like for small business cybersecurity in 2025? It starts with the basics. Regularly updating software may sound mundane, but it closes the door on many common attacks. Password managers help employees avoid the trap of reusing weak passwords, and two-factor authentication adds an extra layer of defense that’s surprisingly effective against credential theft. These are not high-cost, high-tech solutions—they’re accessible Cybersecurity Solutions that any business can implement. The reality is, small businesses don’t need enterprise-level budgets to make meaningful progress. There are now free and affordable tools designed specifically for small business cybersecurity challenges. From automated patch management to cloud-based security suites, the market is full of options that balance cost and protection. The key is to start somewhere, rather than waiting for the “perfect” solution to arrive. Nicole Perlroth, a respected cybersecurity reporter, puts it simply: ‘Small businesses can’t afford to wait for the perfect solution; doing something now is better than nothing.’ This mindset shift—from overwhelm to action—is what builds resilience. Cybersecurity, in many ways, is like flossing. It’s not glamorous, and it rarely feels urgent until something goes wrong. But those small, everyday habits are what keep the most painful problems at bay. Just as skipping flossing leads to bigger dental issues, ignoring basic cybersecurity practices can open the door to costly breaches. Studies indicate that 61% of small and medium businesses were targeted by cyberattacks in 2021, and that number is only expected to rise. Yet, resilience isn’t about heroics or massive investments. It’s about building habits—regular updates, strong passwords, and ongoing Cybersecurity Awareness. These steps, repeated over time, create a strong defense that’s much harder for attackers to penetrate. In the end, the most effective Cybersecurity Solutions for small businesses are the ones that get used. They’re the simple, practical measures that become part of the daily routine. By moving from awareness to action, small businesses can turn daunting cybersecurity challenges into manageable, everyday victories—one smart step at a time. TL;DR: Small businesses are under growing cyber attack in 2025—statistics reveal high risks, costly breaches, and too many are still unprepared. Awareness, proactive security, and practical solutions are essential to avoid becoming the next data breach headline.
13 Minutes Read

Apr 3, 2025
Building a Security-Savvy Workforce: The Key to Human Risk Management
Imagine receiving an email that looks so authentic it could easily be mistaken for a routine work communication. Now, think about how often such emails manage to slip through the cracks of careful scrutiny. This scenario underscores the critical role human error plays in cybersecurity breaches – a reality that became strikingly clear to me during a recent security briefing where a staggering statistic was presented: 85% of breaches involve the 'human element'!Understanding the Human Element in CybersecurityWhen we talk about cybersecurity, we often think of firewalls, encryption, and sophisticated software. But there's another crucial factor at play: the human element. What does this mean? Simply put, it refers to the role that human behavior plays in cyber breaches. It’s a term that encompasses mistakes, negligence, and even malicious actions by individuals within an organization.Defining the Human Element in Cyber BreachesThe human element is a significant contributor to cyber incidents. It includes everything from employees falling for phishing scams to inadvertently sharing sensitive information. In fact, a staggering 85% of cybersecurity breaches involve human elements. This statistic, reported by Verizon, underscores the importance of understanding how human actions can compromise security.Statistics Highlighting the Prevalence of Human ErrorLet’s break this down further. Here are some eye-opening statistics:85% of breaches are due to human error.With the rise of remote work, phishing attacks have surged. Many employees are now working from home, making them more vulnerable to sophisticated attacks.Over the past few years, the frequency of user-targeted attacks has increased dramatically.These numbers reveal a troubling trend. As our work environments evolve, so do the tactics of cybercriminals. They are becoming more adept at exploiting human vulnerabilities.Examples of Recent High-Profile BreachesConsider some recent high-profile breaches that were caused by human mistakes:A major healthcare provider suffered a data breach after an employee clicked on a phishing email, exposing thousands of patient records.A well-known financial institution faced significant losses when an employee mistakenly sent sensitive information to the wrong recipient.In another case, a tech giant experienced a breach due to an employee using a weak password, which was easily guessed by hackers.These incidents illustrate that even the most secure systems can be compromised by human error. It’s a stark reminder that technology alone cannot safeguard against breaches.The Importance of Recognizing Human BehaviorWhy is it essential to recognize the human element in cybersecurity? Because understanding human behavior is key to developing effective security strategies. We need to realize that people are often the weakest link in the security chain. As a cybersecurity expert once said,"The weakest link in cybersecurity is often the human factor."Moreover, the art of deception in phishing has become increasingly sophisticated. Cybercriminals are no longer sending generic emails. They craft messages that appear legitimate, often mimicking trusted sources. This makes it harder for employees to spot a scam.Building a Security-Savvy WorkforceSo, what can organizations do? The answer lies in education and training. By investing in ongoing Human Risk Management (HRM), businesses can:Reduce employee errors that lead to breaches.Enhance data loss prevention by increasing resilience against targeted attacks.Demonstrate compliance with key security frameworks.In conclusion, the human element is a critical factor in cybersecurity. As we navigate an increasingly digital world, we must prioritize training and awareness. After all, protecting our data is not just about technology; it’s about people.Implementing Human Risk Management (HRM) StrategiesOverview of HRM and Its ObjectivesHuman Risk Management (HRM) is not just a buzzword; it’s a vital strategy for today’s businesses. At its core, HRM focuses on understanding and mitigating risks that arise from human behavior. Why? Because, according to Verizon, the ‘human element’ is involved in 85% of cybersecurity breaches. That’s a staggering number!The primary objective of HRM is to create a security-savvy workforce. This means equipping employees with the knowledge and tools they need to recognize and combat cyber threats. It’s about fostering a culture of security awareness that permeates every level of the organization. It’s not just about avoiding breaches; it’s about building resilience.Key Components of an Effective HRM ProgramSo, what makes an HRM program effective? Here are some key components:Education: Regular training sessions are essential. These should be engaging and tailored to the specific needs of your workforce.Assessment: Periodic evaluations, like phishing simulations, help gauge employee vulnerability and reinforce learning.Monitoring: Ongoing dark web monitoring can identify exposed credentials, allowing you to act before an attack occurs.Policy Management: Simplifying processes for tracking employee compliance ensures everyone is on the same page.Each of these components plays a crucial role in reducing human error, which is often the weakest link in cybersecurity.Benefits of HRM in Reducing Breaches and Financial LossesImplementing HRM strategies can lead to significant benefits. Here are a few:Reduction in Breaches: By educating employees, you can significantly lower the chances of breaches caused by human error.Financial Savings: Fewer breaches mean less financial loss. Companies can save on fines and recovery costs.Increased Awareness: As employees become more aware of potential threats, their resilience increases. This is crucial in today’s fast-evolving cyber landscape.As a security consultant once said,“Effective Human Risk Management is not just a program; it's a culture change within the organization.” This statement encapsulates the essence of HRM. It’s about shifting mindsets and behaviors, not just ticking boxes.Aligning HRM with Compliance StandardsAnother important aspect of HRM is its alignment with compliance standards like ISO 27001. This standard emphasizes the importance of risk management in information security. By integrating HRM into your compliance strategy, you not only enhance security but also demonstrate a commitment to best practices.Incorporating HRM into your compliance efforts can streamline processes and ensure that your organization is not just compliant but also secure. This is a win-win situation!Introducing Our Managed HRM ServiceWe’re excited to introduce a new managed HRM service designed to help businesses like yours tackle human cyber risk effectively. This service focuses on:Preventing user-related breaches and financial losses.Strengthening data loss prevention through enhanced employee resilience.Demonstrating compliance with key frameworks.With our service, you can empower your employees and create a robust defense against cyber threats. It’s time to take action and protect your organization from the inside out!Creating a Culture of Cyber AwarenessIn today's digital world, creating a culture of cyber awareness is more important than ever. With the human element playing a role in 85% of cybersecurity breaches, we must prioritize ongoing training and education. But how do we do that effectively?The Role of Ongoing Training and Bite-Sized LearningFirst, let’s talk about ongoing training. It’s not just a checkbox on a compliance list. It’s a necessity. Regular training sessions keep security practices fresh in the minds of employees. Think about it: if you only learned to ride a bike once, would you still be able to ride it years later? Probably not. The same goes for cybersecurity.Bite-sized learning is key. Short, engaging modules make it easier for employees to absorb information.Regular assessments help identify knowledge gaps and reinforce learning.By implementing these strategies, we can transform our workforce into a security-savvy team. Employees become the first line of defense against cyber threats. They need to know how to recognize phishing attempts and other attacks. Regular training ensures they are prepared.Implementing Phishing Simulations EffectivelyNow, let’s dive into phishing simulations. These are crucial for assessing how vulnerable your employees are to attacks. But how do we implement them effectively?Start with a baseline: Before launching simulations, understand your current security posture. This helps in measuring improvement.Create realistic scenarios: Use real-world examples that employees might encounter. This makes the training relatable.Provide immediate feedback: After a simulation, give employees feedback on their performance. This helps them learn from their mistakes.Phishing simulations not only test employees but also educate them. They learn what to look for and how to respond. It’s like a fire drill for cybersecurity. You don’t want to wait until there’s a fire to learn how to escape!Using Dark Web Monitoring to Bolster Employee SecurityAnother vital component is dark web monitoring. This proactive measure identifies exposed user credentials before they can be exploited. It’s like having a security guard watching over your digital assets.Identify risks: Regular monitoring helps you spot compromised credentials.Prevent attacks: By addressing these vulnerabilities, you can prevent potential breaches.Imagine finding out that your employees' credentials are for sale on the dark web. Wouldn’t you want to act immediately? Dark web monitoring allows us to do just that, giving us a chance to strengthen our defenses before an attack occurs.“Training shouldn't be a one-time event; it needs to be continuous and evolving.” - Cybersecurity TrainerIncorporating these elements into your cybersecurity strategy can significantly enhance your organization’s resilience. By focusing on ongoing training, effective phishing simulations, and dark web monitoring, we can create a culture of cyber awareness that empowers employees. They become not just participants but champions of cybersecurity.Let’s explore interactive training sessions and simulations that strengthen employee cybersecurity awareness. Together, we can build a safer digital environment for everyone.Assessing Your Human Cyber Risk with a Human Risk ReportIn today’s digital landscape, the human element is often the weakest link in cybersecurity. Did you know that a staggering 85% of cyber security breaches involve human error? This highlights the urgent need for businesses to understand their vulnerabilities. One effective tool for this is the Human Risk Report (HRR). But what exactly is an HRR, and how can it help your organization?What is a Human Risk Report (HRR)?A Human Risk Report is a comprehensive analysis that identifies and assesses the human-related risks within your organization. It provides insights into how employees interact with security protocols and where they might fall short. The HRR helps highlight specific areas of risk, allowing organizations to set benchmarks for improvement.Think of it this way: if your organization were a ship, the HRR would be the compass guiding you through treacherous waters. It shows you where the leaks are and helps you patch them up before they sink your ship.Steps to Claim and Benefit from a Free HRRClaiming your free Human Risk Report is straightforward. Here’s how you can get started:Visit the website: Go to this link.Fill out the form: Provide the necessary details about your organization.Receive your report: Once submitted, our team will analyze your business for vulnerabilities and send you the HRR.By following these simple steps, you can gain valuable insights into your organization’s human cyber risk. The report will not only identify weaknesses but also provide actionable recommendations to strengthen your security posture.Understanding Potential Vulnerabilities in Your OrganizationEvery organization has its unique set of vulnerabilities. These can stem from various sources, including:Employee behavior: Poor password practices or falling for phishing scams.Lack of training: Employees may not be aware of the latest threats or best practices.Outdated policies: Security protocols that haven’t been updated can leave gaps.Understanding these vulnerabilities is crucial. As the saying goes,“Knowledge is power; understanding where your risks lie is crucial to building resilience.” - Cybersecurity Analyst The HRR provides a clear picture of where your organization stands and what steps you can take to improve.Moreover, the essentials included in the report have a significant impact on your overall security posture. By addressing the highlighted areas, you can prevent user-related breaches, fines, and financial losses caused by human error. This proactive approach not only protects your organization but also builds a culture of security awareness among your staff.In conclusion, the Human Risk Report is an invaluable tool for any organization looking to bolster its cybersecurity defenses. By understanding and addressing human-related risks, you can create a more resilient workforce. So, why wait? Take the first step towards securing your organization by claiming your free HRR today. It’s time to turn knowledge into action and safeguard your business from potential threats.TL;DR: To protect against cyber threats, businesses must implement ongoing Human Risk Management strategies that educate employees on security practices and build resilience against attacks.Claim your Free Human Risk Report
10 Minutes Read

Mar 17, 2025
Cyber Hygiene: The Key to Safeguarding Your Business in a Digital World
I still remember the sinking feeling when I discovered my friend's business had fallen victim to a cyber attack. The impact was devastating, but what was even more shocking was that simple cyber hygiene practices could have prevented it. This incident lit a fire in me to unravel the complexities of cybersecurity for businesses and how small adaptations can lead to remarkable changes in safety. This blog is dedicated to helping others navigate through the murky waters of cyber threats with confidence and ease. Understanding Cyber Hygiene: The Basics In today's digital world, understanding cyber hygiene is crucial. But what exactly is it? Simply put, cyber hygiene refers to the practices that help maintain the health of your systems. Just like we take care of our physical health, we need to take care of our digital health. This is especially important for businesses. After all, a single breach can lead to devastating consequences. Why is Cyber Hygiene Important for Businesses? Let’s face it: we live in a time where cyber threats are everywhere. From phishing scams to ransomware attacks, the risks are real. Neglecting basic cyber hygiene can leave your organization vulnerable. Here are a few reasons why it matters: Protection of Sensitive Data: Businesses handle a lot of sensitive information. This includes customer data, financial records, and intellectual property. Poor cyber hygiene can lead to data breaches, which can be costly. Reputation Management: A breach can tarnish your reputation. Customers trust you with their information. If you fail to protect it, they might take their business elsewhere. Compliance Requirements: Many industries have regulations regarding data protection. Failing to adhere to these can result in hefty fines. As a business owner, I often wonder: how much are we truly doing to protect our digital assets? It’s a question we should all ask ourselves regularly. Common Vulnerabilities from Poor Cyber Hygiene Now that we understand the importance of cyber hygiene, let’s discuss some common vulnerabilities that arise when it’s neglected: Weak Passwords: Using simple or easily guessable passwords is a major risk. It’s like leaving your front door wide open. Outdated Software: Failing to update software can expose you to known vulnerabilities. Cybercriminals often exploit outdated systems. Lack of Employee Training: Employees are often the weakest link in cybersecurity. Without proper training, they may fall for phishing scams or mishandle sensitive information. In my experience, I’ve seen firsthand how a simple oversight can lead to significant issues. For instance, a colleague once clicked on a suspicious link in an email. It turned out to be a phishing attempt. Thankfully, we caught it in time, but it was a wake-up call for all of us. What Cyber Hygiene Means in the Workplace So, what does cyber hygiene look like in practice? It’s about creating a culture of awareness and responsibility. Here are some key practices: Regular Software Updates: Ensure that all software is updated regularly. This includes operating systems, applications, and antivirus programs. Strong Password Policies: Implement policies that require strong, unique passwords. Encourage the use of password managers. Employee Training: Regularly train employees on cybersecurity best practices. Make them aware of the latest threats. As I reflect on my own workplace, I realize that we’ve made strides in improving our cyber hygiene. We hold regular training sessions and have implemented strong password policies. Yet, there’s always more to learn and improve upon. "Cyber hygiene is as essential as regular health checkups; you never know what's lurking until you look closely." - Cyber Expert In conclusion, maintaining good cyber hygiene is not just a technical requirement; it’s a fundamental part of running a successful business. By understanding its importance, recognizing common vulnerabilities, and implementing best practices, we can better protect our digital assets. Remember, in the world of cybersecurity, an ounce of prevention is worth a pound of cure.The Role of Employee Training in Cybersecurity When we think about cybersecurity, we often picture firewalls, encryption, and advanced software. But what about the people behind the screens? Employees are often the first line of defense in any cybersecurity strategy. Yet, many of them lack the necessary knowledge to recognize and respond to threats. This gap in knowledge can lead to devastating consequences for organizations. Identifying Knowledge Gaps Let’s face it: many employees don’t fully understand the risks they face every day. Here are some common gaps in knowledge: Phishing Scams: Many employees may not recognize a phishing email. They might click on a link, thinking it’s legitimate. Weak Password Practices: Employees often use simple passwords or reuse them across multiple accounts. This makes it easy for hackers. Social Engineering: Some employees may not be aware of how social engineering works. They might unknowingly give away sensitive information. These gaps can be filled with effective training programs. But how do we create a culture of security within our organizations? Effective Strategies for Employee Training Programs Training isn’t just a one-time event. It should be ongoing and engaging. Here are some strategies that can help: Interactive Workshops: Instead of boring lectures, use interactive workshops. Role-playing scenarios can help employees practice what to do in real-life situations. Regular Updates: Cyber threats evolve quickly. Regularly update training materials to reflect the latest threats and trends. Gamification: Incorporate game-like elements into training. This can make learning fun and memorable. Real-Life Examples: Share stories of actual breaches. This makes the threat more tangible and relatable. By implementing these strategies, we can empower employees to take cybersecurity seriously. As the saying goes, “An organization is only as strong as its weakest link, often the employee who is not properly trained.” - Cybersecurity Analyst Success Stories from Robust Training Programs Many companies have seen the benefits of investing in employee training. Here are a few success stories: Company A: After implementing a comprehensive training program, Company A reduced phishing incidents by 70%. Employees became more vigilant and aware of potential threats. Company B: This company introduced gamified training modules. Employee engagement increased, and they reported a 50% improvement in password security practices. Company C: By sharing real-life breach stories, Company C created a culture of accountability. Employees felt responsible for protecting sensitive information. These examples show that training is essential for enabling employees to recognize and respond to threats appropriately. It’s not just about protecting the company; it’s about creating a safer environment for everyone. Building a Culture of Security Regular training helps to build a culture of security within an organization. It’s not just a checkbox on a compliance list. It’s about fostering an environment where everyone feels responsible for cybersecurity. How can we achieve this? Here are some tips: Encourage Open Communication: Create a space where employees can report suspicious activities without fear of repercussions. Lead by Example: Management should participate in training. When leaders prioritize cybersecurity, employees will follow suit. Recognize and Reward: Acknowledge employees who demonstrate good cybersecurity practices. This reinforces positive behavior. In conclusion, employee training is not just a necessity; it’s a vital part of any cybersecurity strategy. By addressing knowledge gaps, implementing effective training programs, and sharing success stories, we can create a more secure workplace for everyone.Building Business Protection Strategies: An Essential Blueprint In today’s world, where technology is at the forefront of everything we do, protecting our businesses from cyber threats is crucial. The stakes are high. Cyber threats can disrupt operations, damage reputations, and lead to significant financial losses. So, how can we safeguard our businesses effectively? Let’s dive into the critical elements of business protection measures against cyber threats. Understanding Cyber Threats First, we need to recognize what we’re up against. Cyber threats come in various forms, including: Malware Phishing attacks Ransomware Data breaches Each of these threats can have devastating effects. For instance, a ransomware attack can lock you out of your own data, demanding a hefty ransom to regain access. It’s like being held hostage, but in the digital realm. Critical Elements of Business Protection To combat these threats, businesses need a multi-layered approach to cybersecurity. This includes: Software Solutions: Invest in robust antivirus and anti-malware software. These tools act as your first line of defense. Policies and Procedures: Establish clear cybersecurity policies. Make sure everyone in your organization knows the rules. Employee Training: Regularly train employees on cybersecurity best practices. They are often the first line of defense against cyber threats. Think of it this way: just like a castle needs strong walls, a business needs solid cybersecurity measures to protect its valuable assets. Enhancing Business Resilience Integrating cybersecurity solutions can significantly enhance business resilience. But what does that mean? It means that when a cyber incident occurs, your business can recover quickly and effectively. Here’s how you can achieve this: Regular Backups: Always back up your data. This way, if you do face a cyber attack, you won’t lose everything. Incident Response Plan: Develop a clear plan for responding to cyber incidents. This should include who to contact and what steps to take. Continuous Monitoring: Implement systems that continuously monitor your network for unusual activity. Early detection can prevent major breaches. As an industry leader once said, "In the digital age, proactive business protection is not an option, but a necessity." This couldn’t be more accurate. Actionable Steps for Cybersecurity Enhancement Now that we understand the critical elements and how to enhance resilience, let’s look at some actionable steps you can take to improve your cybersecurity posture: Conduct a Risk Assessment: Identify your vulnerabilities. What areas are most at risk? Implement Strong Password Policies: Encourage the use of complex passwords and change them regularly. Use Multi-Factor Authentication: This adds an extra layer of security. Even if a password is compromised, your data remains safe. Stay Updated: Regularly update software and systems. Cybercriminals often exploit outdated software. By taking these steps, we can create a safer environment for our businesses. Conclusion In conclusion, building effective business protection strategies is not just about having the right tools. It’s about creating a culture of cybersecurity awareness. A comprehensive cybersecurity strategy is vital for any modern business. As we’ve discussed, investing in cybersecurity can lead to long-term savings by preventing breaches and data loss. Remember, the digital landscape is constantly evolving, and so should our defenses. Let’s stay aware, stay smart, and stay secure. Together, we can build a safer future for our businesses.TL;DR: Cyber hygiene is critical for business safety, and effective training for employees is key. MyCyberIQ emphasizes practical strategies to ensure a secure digital environment.
9 Minutes Read
